WHAT IS 2 FACTOR AUTHENTICATION? and why its so important!
Posted by Tehillah Mwakalombe on 28th Jun 2022
Before we answer the question ‘what is two-factor authentication’ or ‘what is 2FA,’ let’s consider why it’s important to do everything you can to improve your online account security.
With so much of our lives happening on mobile devices and laptops, it explains why our digital accounts have become a magnet for criminals. Malicious attacks against governments, companies, and individuals are getting more and more common.
Luckily, it’s easy for businesses to add an extra level of protection to user accounts in the form of two-factor authentication, also commonly referred to as 2FA.

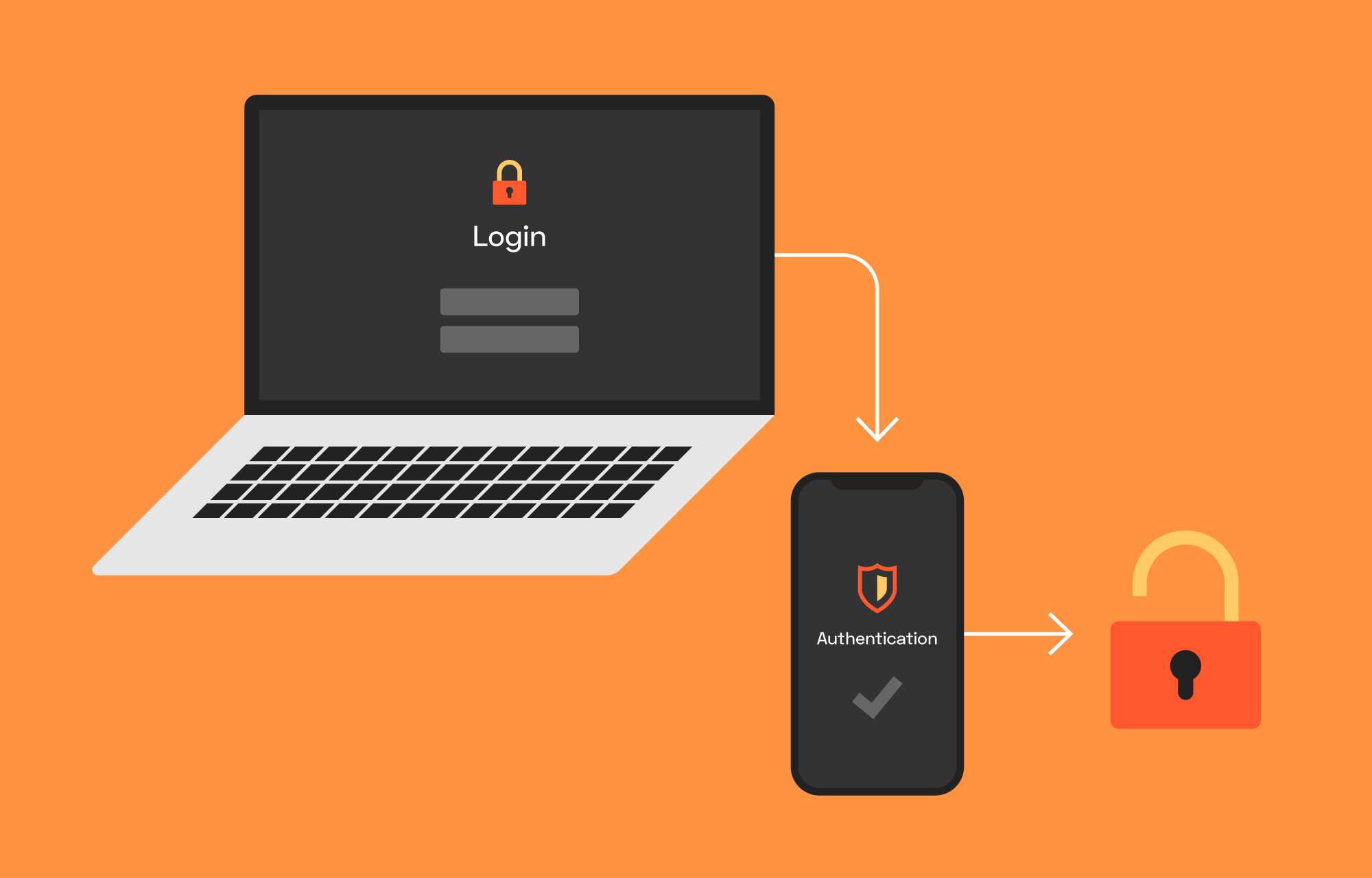
2FA is an extra layer of security used to make sure that people trying to gain access to an online account are who they say they are. First, a user will enter their username and a password. Then, instead of immediately gaining access, they will be required to provide another piece of information. This second factor could come from one of the following categories:
Personal Fact: This could be a personal identification number (PIN), a password, answers to “secret questions” or a specific key pattern
Possession: Typically, a user would have something in their possession, like a credit card, a smartphone, or a small hardware token
Biometric: This category is a little more advanced, and might include biometric pattern of a fingerprint, an iris scan, or a voice print
With 2FA, a change of just one of these factors won’t unlock the account. So, even if your password is stolen or your phone is lost, the chances of someone else having your second-factor information is highly unlikely.

If a site you use only requires a password to get in and doesn’t offer 2FA, there’s a good chance that it will be eventually be hacked. That doesn’t mean that all 2FA is the same.
Several types of two-factor authentication are in use today; some may be stronger or more complex than others, but all offer better protection than passwords alone. Let’s look at the most common forms of 2FA.

SMS Text-Message and Voice-based
SMS-based 2FA interacts directly with a user’s phone. After receiving a username and password, the site sends the user a unique one-time passcode (OTP) via text message. Then the user must then enter the OTP back into the application before getting access.
Similarly, voice-based 2FA automatically dials a user and verbally delivers the 2FA code. While not common, it’s still used in countries where smartphones are expensive, or where cell service is poor.

Software Tokens
The most popular form of two-factor authentication (and a preferred alternative to SMS and voice) uses a software-generated time-based, one-time passcode (also called TOTP, or “soft-token”).
First, a user must download and install a free 2FA app on their smartphone or desktop. They can then use the app with any site that supports this type of authentication.
At sign-in, the user first enters a username and password, and then, when prompted, they enter the code shown on the app, the soft-token is typically valid for less than a minute. And because the code is generated and displayed on the same device, soft-tokens remove the chance of hacker interception. That’s a big concern with SMS or voice delivery methods.

Push Notification
Rather than relying on the receipt and entry of a 2FA token, websites and apps can now send the user a push notification that an authentication attempt is taking place. The device owner simply views the details and can approve or deny access with a single touch. It’s passwordless authentication with no codes to enter, and no additional interaction required.
By having a direct and secure connection between the retailer, the 2FA service, and the device, push notification eliminates any opportunity for phishing, man-in-the-middle attacks, or unauthorized access.
But it only works with an internet-connected device, one that’s able to install apps
In conclusion, 2 factor authentication is an extremely helpful feature and we recommend everyone implements it on all their accounts! In our next blog, we’ll show you how to step it up for your online personas.

